The evident rise of digital asset adoption is directly proportional to the rise of institutional participation, aiding and abetting the cause of making them easily accessible and safe to operate, following the standard norms of compliance.
With the pace at which institutions are throwing liquidity in the market, amping up the count for daily transactions made, the need for building user-compatible applications, stringent monitoring engines, and fully customized workflow processes to detect anomalies becomes inevitable for the digital assets market.
Currently, most institutions managing their wallets on either a self-custody infrastructure or integrated with a qualified digital asset custodian manually drive transaction monitoring, leading to bottlenecks and missed opportunities in detecting risks.
Unlock the potential of digital assets for your institution
Unlock the potential of digital assets for your institution
This problem arises primarily for such institutions’ security and compliance teams, whether they should run behind increased security or strive for efficiency.
Enter Liminal Firewall–a dynamic, policy-based solution designed to secure and automate digital asset transactions by monitoring them for risk and compliance checks for your custody account.
Aimed at solving complexities involved in institutional wallets and automating the process of checking transactions for risk and compliance based checks.
Understanding risks in institutional transactions
For institutions, the risk profiles for each transaction are different; that needs not a standard rule of checks to identify and eliminate them, but a more customized approach.
Secure and manage your digital assets with Liminal
The spectrum of vulnerabilities in digital asset transactions is vast. It includes anomalies in transactions that may signal market manipulation, irregularities in compliance checks that could expose institutions to risk, and even the potential for fraudulent actors to divert funds to illicit addresses. Tackling these challenges requires a comprehensive and strategic approach.
Risk assessment doesn’t stop at secure transactions. As operations expand, automation becomes crucial. It streamlines workflows, identifies potential security and compliance issues, and facilitates efficient monitoring, ultimately leading to a more robust risk management system.
But, building a middleware solution is just as hard as building a completely secure network for institutional wallets.
Liminal Firewall Engine
Securing Transactions Dynamically
Liminal’s Firewall introduces dynamic policy control to your organization’s transactions. By screening them against multiple parameters, it ensures that every transaction, whether incoming or outgoing, meets the highest standards of security and compliance.
The Intuitive Rule Engine
Using Liminal’s intuitive rule engine, craft policies that align with your business risk profile. These fully customized, rule-based policies track and approve transactions, pre-screening them for security, compliance, and anomaly threats before reaching the signer.
Ensuring Travel Rule and KYT Compliance
Leverage Liminal’s built-in integration with compliance providers like Notabene, TRM Labs, and Elliptics. This integration facilitates seamless adherence to travel rules and Know Your Transaction (KYT) compliance, automating your entire compliance operation according to jurisdictional requirements.
Secure and manage your digital assets with Liminal
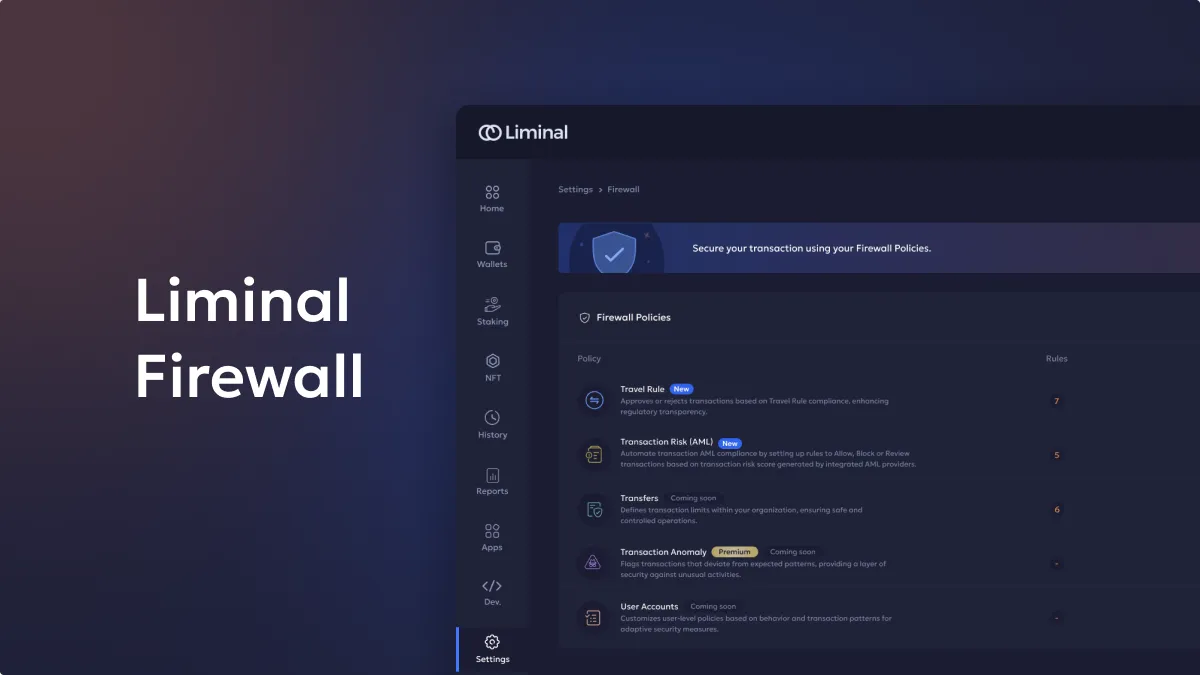
Customizing Firewall Policies for Your Needs
Customize firewall policies to meet your specific needs, regardless of the transaction type or scale. Explore key policies:
1. Transfer Policy Coming Soon:
- Define transfer and withdrawal limits: Set maximum amounts for individual transfers and withdrawals based on asset type. This prevents unauthorized large-scale movements and helps manage operational risks.
- User can limit transaction by per hours in USD, by per Day in USD, and by per Transaction in USD in one request
2. Travel Rule Policy:
- Secure data sharing: Integrate with Travel-Rule compliant platforms to securely share data with other VASPs (Virtual Asset Service Providers) as mandated by regulations.
3. Transaction Risk Policy:
- Real-time risk assessment: Implement real-time transaction monitoring to identify and flag suspicious activities based on defined risk parameters.
- Customizable risk factors: Tailor risk parameters to your specific requirements and risk tolerance, ensuring a balanced security and operational efficiency approach.
- Automated alerts and notifications: Receive immediate alerts about high-risk transactions, allowing for swift intervention and investigation if necessary.
How does Liminal Firewall work?
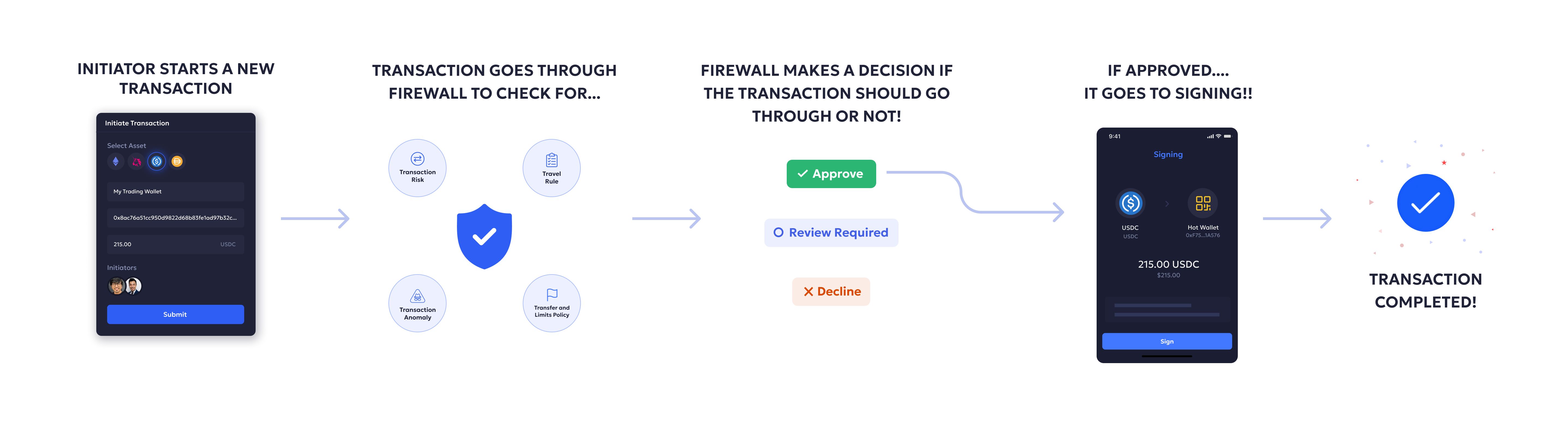
Imagine a seamless flow that empowers security and compliance teams. Liminal Firewall sits at the critical juncture, monitoring all the inbound and outbound transactions to check if they come under the risk parameter or execute if they pass the parameter.
- Policy Setup: Tailored, custom policies are established to counter key threats.
- Automatic Enforcement: The policies are enforced automatically, eliminating the margin for manual errors.
- Integration: Liminal Firewall integrates compliance and risk-checking mechanisms.
- Initiation: Transaction starts within the institutional workflow.
- Liminal Firewall Analysis: Real-time analysis of transaction details against predefined policies.
- Policy Enforcement: Automatic application of tailored policies to mitigate risks.
- Decision Categorization: Transaction goes through three categories of Allow, Reject, and Approval requested
- Signing: If the transaction gets approved or allowed for all parameters, it goes to the signing phase
Integration with Notabene & TRM Labs for compliance checking
From compliance giants to technology pioneers, Liminal Firewall unites the best minds in the industry. This collaborative spirit fuels our commitment to your digital asset security.
- Travel Rule by Notabene: Strengthening cross-border transactions.
- KYT/AML by TRM Labs: Elevating identity verification and anti-money laundering measures.
Reinforce Your Security and Compliance
The surge in digital asset adoption has propelled institutional involvement, emphasizing the necessity for accessible and secure operations aligned with compliance standards. As transaction volumes escalate, the demand for better automation tools to track and mitigate transactional risks becomes imperative.
Building a secure institutional wallet and digital asset custody infrastructure at Liminal, configured with an advanced automation engine, our Firewall engine is another step in the process of fast-pacing the everyday operational tasks for security and compliance teams.
Understanding the multifaceted risks associated with institutional transactions underscores the importance of customized risk assessment and management approaches. Liminal Firewall’s intuitive rule engine and comprehensive policies empower organizations to fortify transaction security, ensure compliance with regulations such as the Travel Rule and KYT/AML, and mitigate various threats effectively.
Learn more about Liminal Firewall >>